Data and information security in public administration
How can the NIS2 directive be successfully implemented in public administration? This industry solution highlights the challenges and solutions and provides practical recommendations for your security.
NIS2
Security and resilience for the future
Secure administration and strong data protection are compatible. With 4conform, public authorities reliably meet all IT and data protection requirements and effectively protect citizen data.
Public administration faces the challenge of reliably protecting sensitive citizen data and critical infrastructures. At the same time, requirements are constantly increasing due to laws such as NIS2, the IT Security Act and the GDPR.
With the 4conform ENTERPRISE solution for ISMS and DSMS, we support authorities in detecting cyberattacks at an early stage, implementing data protection seamlessly and managing processes efficiently. This not only ensures compliance, but also strengthens citizens’ trust in your administration.
Data protection & information security
The 9 most important challenges for public administration
Ransomware attacks
Cybercriminals encrypt your data and demand a ransom. Such an attack can lead to business interruptions, financial losses and reputational damage. SMEs are often seen as easy targets, which increases the danger.
Phishing attacks
Employees are tricked into disclosing sensitive data by fake emails or messages. These attacks are often difficult to detect and can lead to data loss and financial damage.
Denial of service attacks (DoS)
The accessibility of your online services is blocked by targeted attacks. This can lead to lost sales and a loss of customer confidence.
Outdated IT infrastructures
Old systems and software with unpatched security vulnerabilities offer attack surfaces, which is particularly critical for networked management systems. Modern security standards often cannot be implemented.
GDPR compliance
High documentation requirements, reporting obligations within 24 hours and transparency requirements overburden many authorities organizationally. Legal uncertainties regarding data pools increase the risk.
Scarcity of resources
A lack of IT security experts and insufficient budgets are hampering investment in modern protection measures. Uncompetitive salaries exacerbate the problem.
External service provider risks
Cloud services and outsourcing partners without sufficient security certifications jeopardize compliance. Contract design with external providers is often inadequate.
Employee sensitization
Ignorance of phishing methods and insecure handling of data lead to avoidable security incidents. Regular training is often lacking.
Emergency planning
Unclear escalation paths in the event of data breaches and inexperienced communication with those affected exacerbate the consequences of security incidents.
If you would like more detailed information on the NIS2 law, we recommend our NIS2 AI Co-Advisor or refer to the current NIS2 EU Regulation or the draft law of the Austrian Federal Government.
ISMS Live
Take a look at our ISMS in action
As the person responsible for information security, you face the challenge of managing risks quickly and efficiently without losing track of the bigger picture.
This is exactly where we come in – not at some point, but right now. See for yourself in our short video or the guided tour on WebinarGeek.
An example
Dangers in public administration
Public institutions are disproportionately often the target of cyberattacks, particularly ransomware. On average, two municipalities were affected per month in 2023, with consequential costs of up to €2.6 million per incident.
Example 1: Carinthian state administration (May 2022)
A ransomware attack paralyzed the IT infrastructure of the state of Carinthia. Attackers broke in via a workstation, encrypted servers and published 5.6 GB of sensitive data (including passports) on the darknet. The ransom demand amounted to 5 million euros. The Court of Audit criticized the incomplete IT security management. However, 5.75 million euros were invested in recovery measures.
Example 2: Municipality of Tulln (February 2025)
A cyberattack encrypted the server infrastructure, which meant that citizen services such as notarizations were only possible to a limited extent for weeks. External IT companies and the security authorities analyzed the damage. Data misuse could not be ruled out. The reason was a security gap in the firewall, which the hacker group was able to use to gain access.
Proactive risk analyses
Regular vulnerability analyses and threat modelling identify critical IT risks (e.g. outdated systems, unsecured interfaces) in order to prioritize targeted protective measures against attacks.
Incident response plans
Clear escalation processes, reporting chains and communication routines enable rapid action in the event of security incidents in order to minimize downtime and consequential damage.
Robust backup strategies
Backups, immutable storage and regular recovery tests protect against data loss – even in the event of ransomware attacks, backed-up data remains intact and can be restored quickly.
Take back control of your cybersecurity with 4conform ENTERPRISE ISMS. Our comprehensive solution helps you build a robust and customized information security management system that detects threats early, protects your critical infrastructure and helps you meet complex regulatory requirements – to keep the lights on safely.
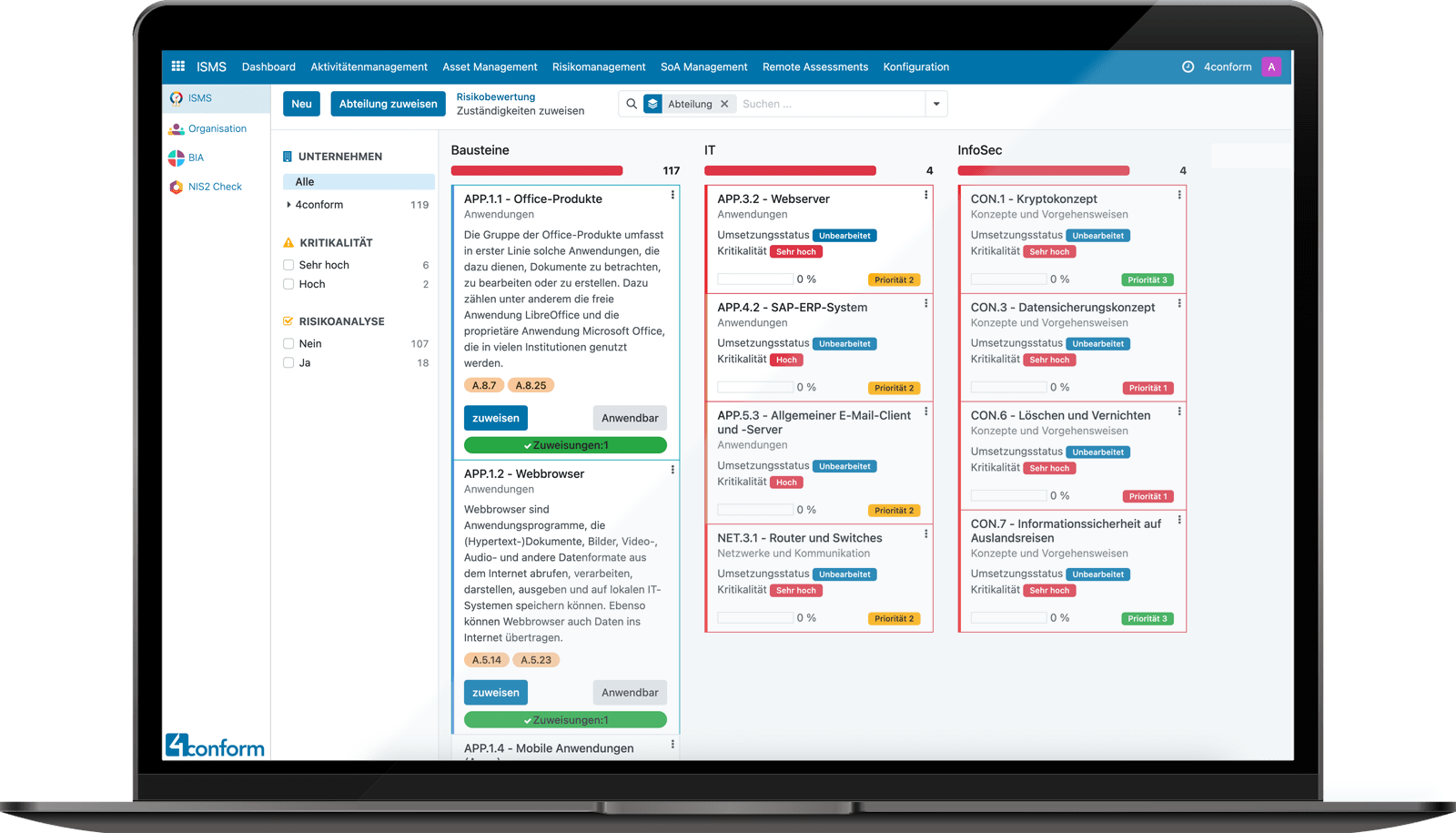
Keep an eye on all departments and their risks.
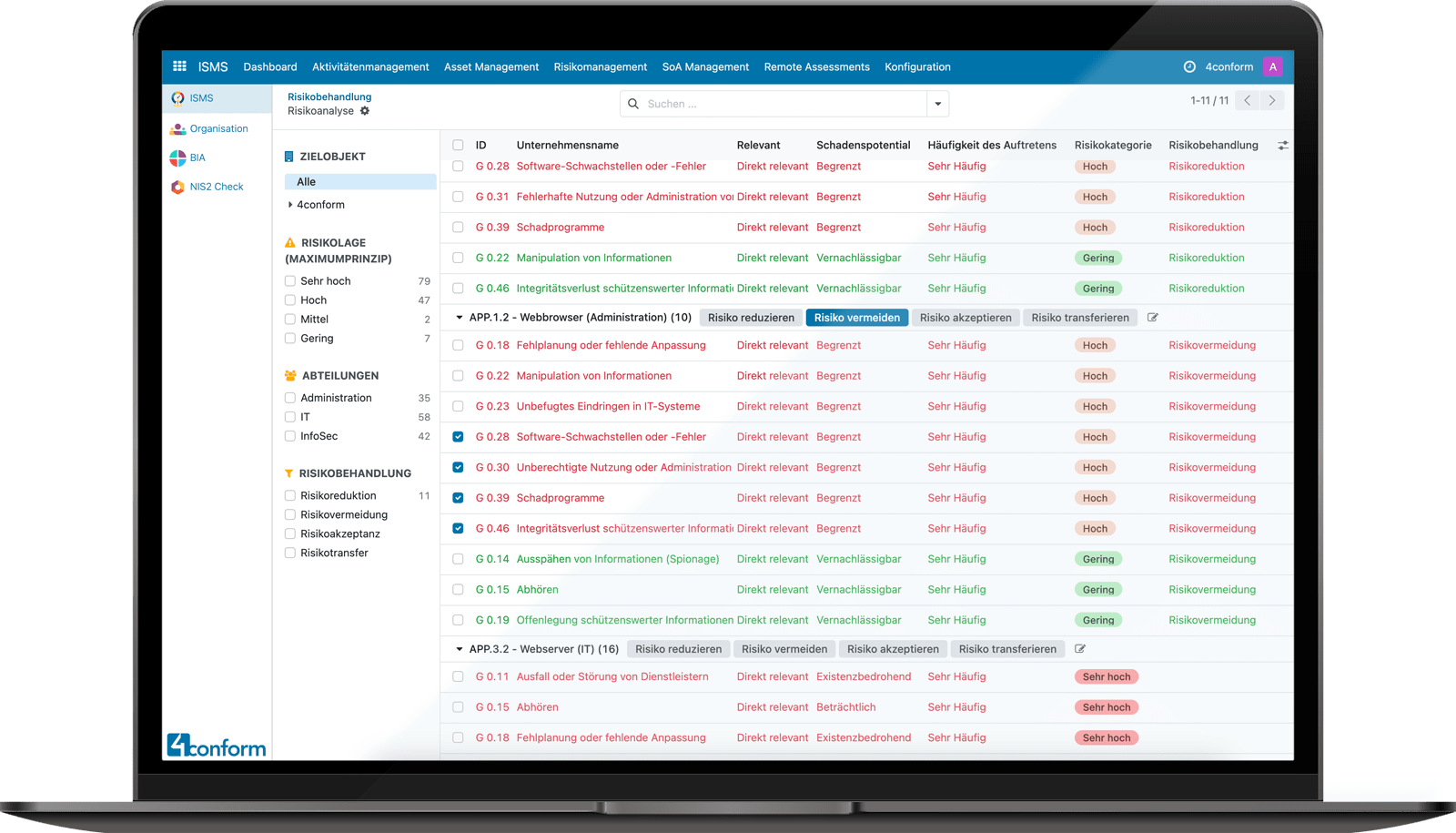
Risk treatment of all hazards for your company.
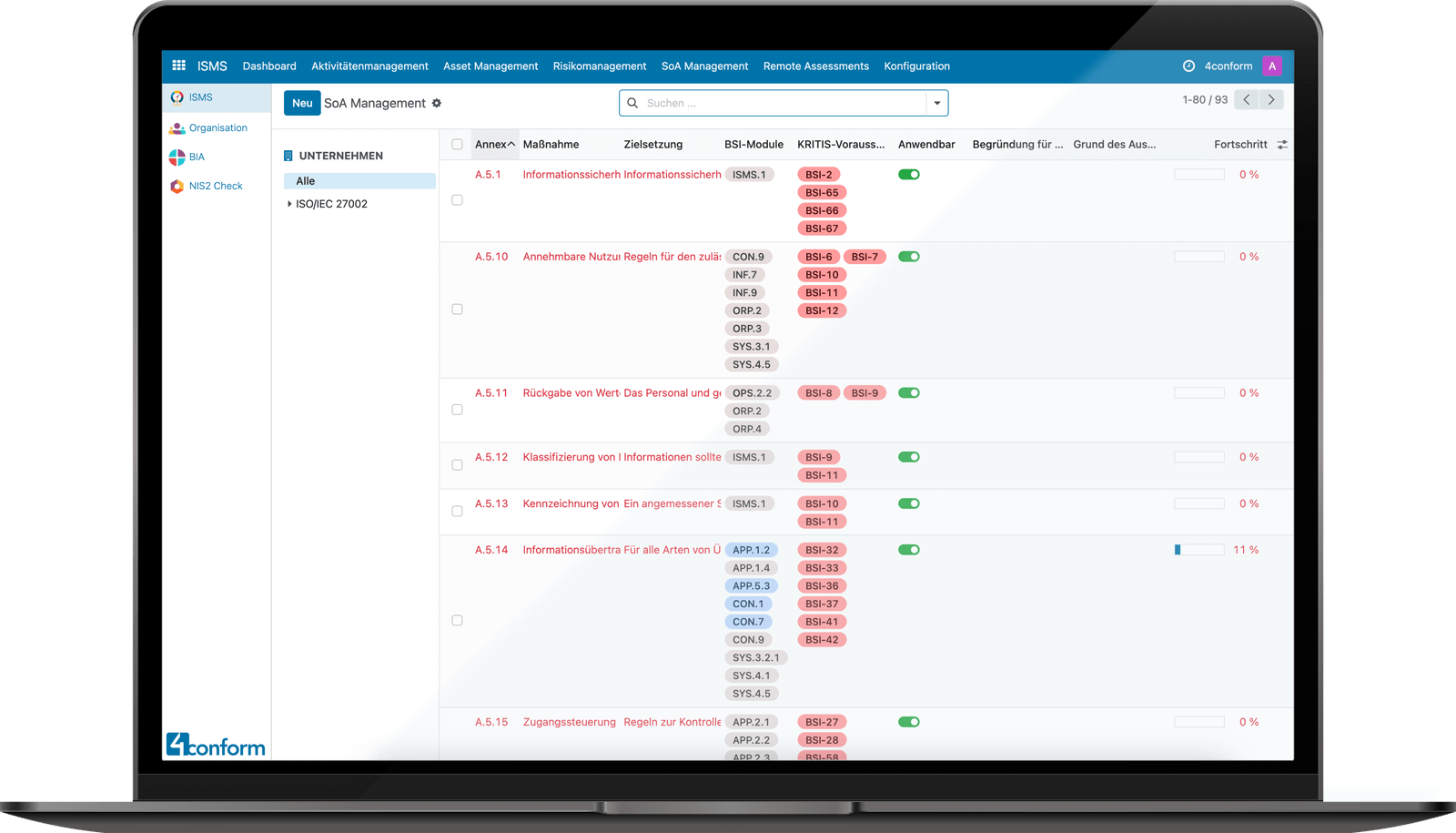
Statement of applicability in 4conform ENTERPRISE ISMS als Checkliste.
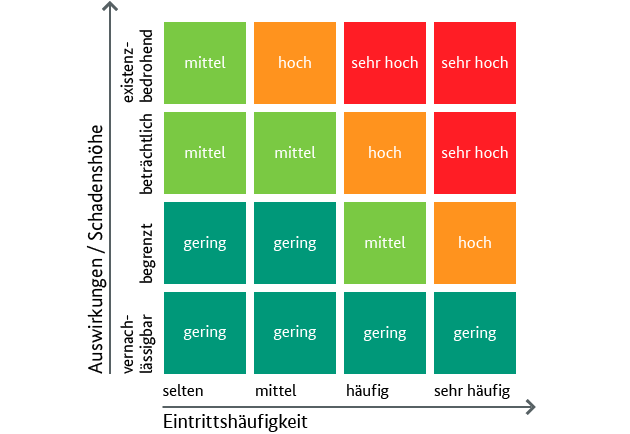
Classify your risks with the help of the BSI risk matrix.
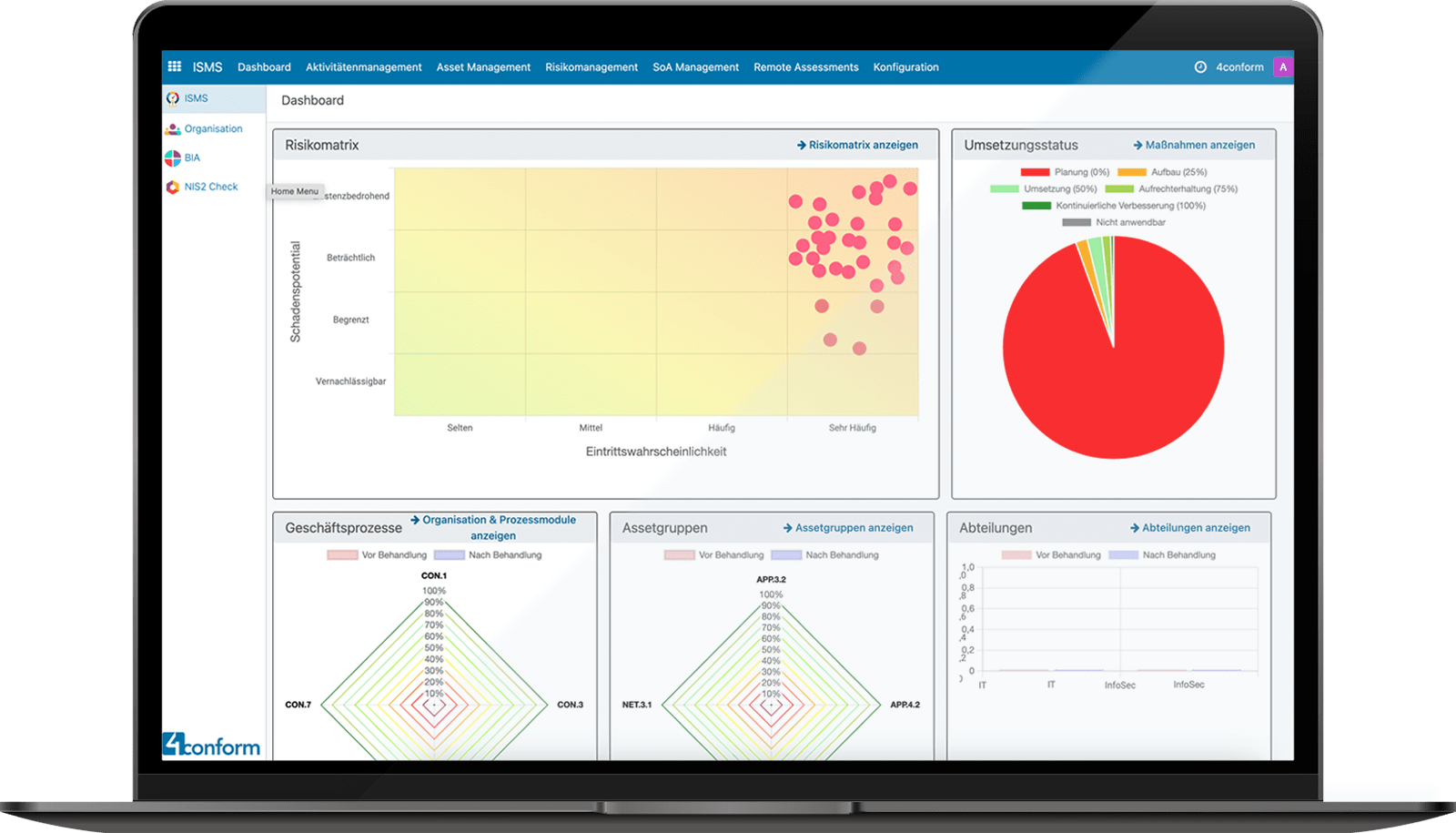
The risk matrix in the 4conform ENTERPRISE ISMS dashboard
Information security
How can our ISMS help?
A structured information security management system (ISMS) is essential for public institutions. It enables those responsible to effectively protect critical infrastructures such as government IT, digital citizen services and sensitive data from cyber threats.
For example, an ISMS supports the security of administrative systems, compliance with authority-specific requirements (e.g. BSI IT baseline protection), precise risk management in the event of targeted attacks and a rapid response to security incidents. With an ISMS, public institutions improve their organizational security, ensure the integrity and availability of citizen data and increase their resilience to cyberattacks.
This strengthens the administration’s ability to act and citizens’ trust in digital services. Investments in an ISMS make public infrastructures future-proof and NIS2-compliant.
BSI basic protection included
Start your ISMS without detours! Our 4conform ENTERPRISE ISMS software contains all relevant BSI basic protection modules with the corresponding measures.
This means you can get started right away. Rely on a proven solution that saves you time, resources and headaches. Secure your company with an ISMS that has been developed by experts and meets the highest standards.
What benefits does an ISMS offer?
4conform ENTERPRISE ISMS is used specifically to make managing your information security easier and more efficient. It serves as a central platform to support processes relating to information security, risk and compliance management.
Data protection
How can our DSMS help you?
For public administration, which is considered critical infrastructure under the NIS2 Directive, a comprehensive data protection management system (DSMS) is essential to ensure the security and integrity of sensitive data (e.g. citizen data, tax information). Specialized solutions such as 4conform ENTERPRISE DSMS support public authorities in making all data processing processes NIS2 and GDPR compliant and protecting the privacy of citizens.
A DSMS strengthens trust in government services, reduces legal risks and ensures the reliability of critical systems. By implementing a DSMS, public institutions can not only achieve compliance, but also avoid disruptions in provision (e.g. failure of registration offices, social benefit systems). This is crucial to ensure the continuity of public services, which are essential for the functioning of society and the economy.
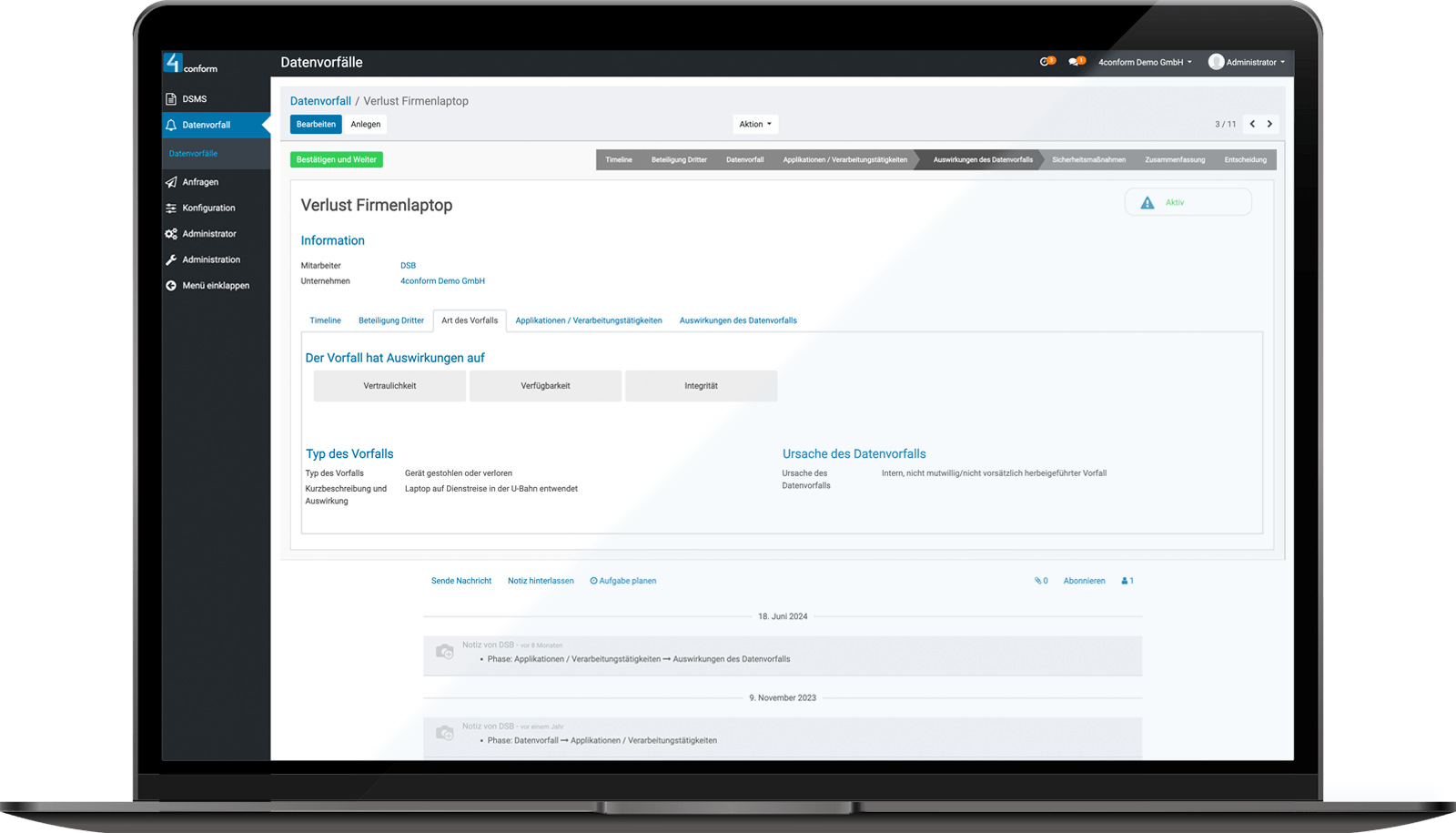
Process data incidents easily and in compliance with the law in ENTERPRISE DSMS.
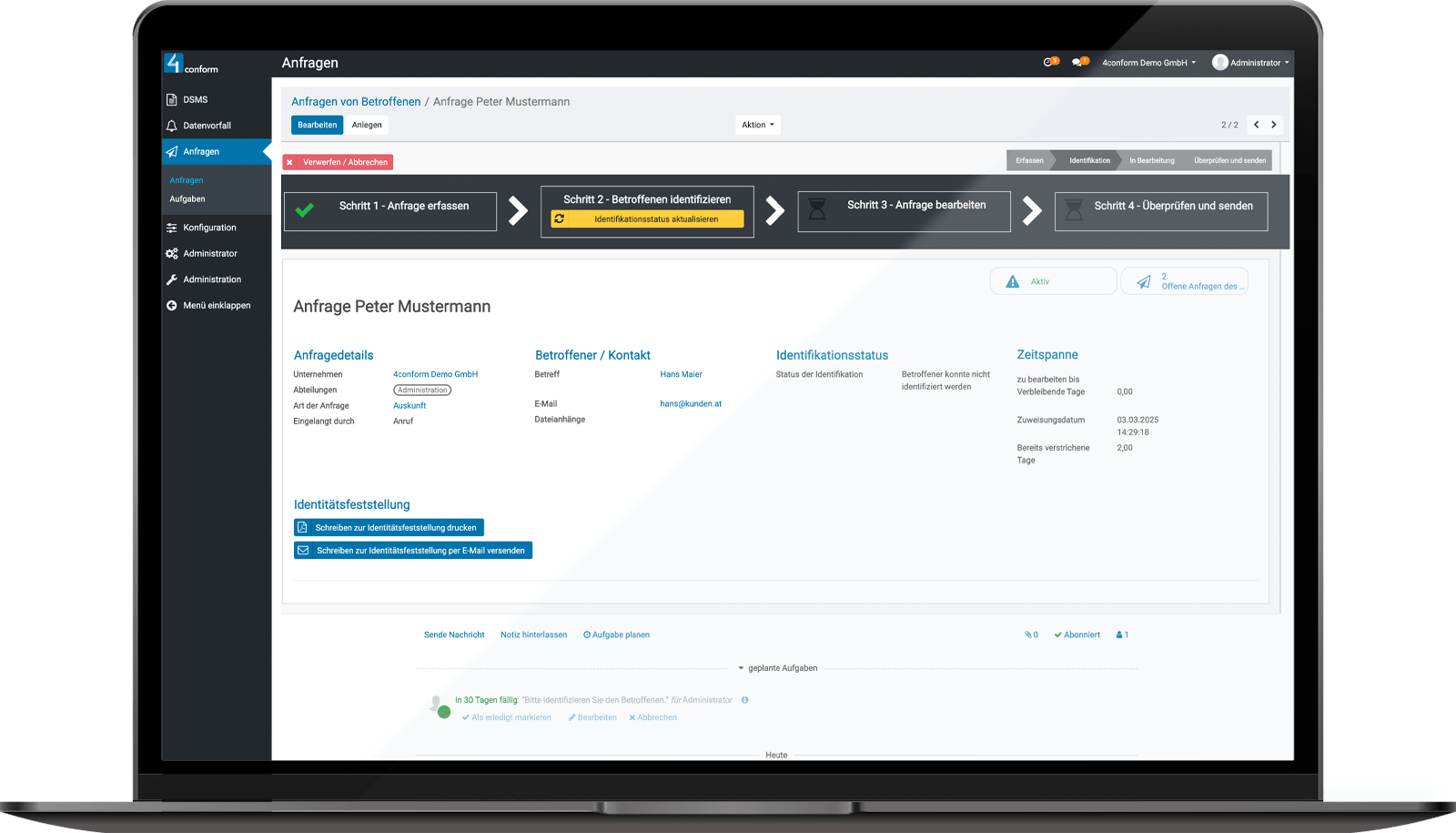
Manage and process your data subject requests in accordance with the legal requirements.
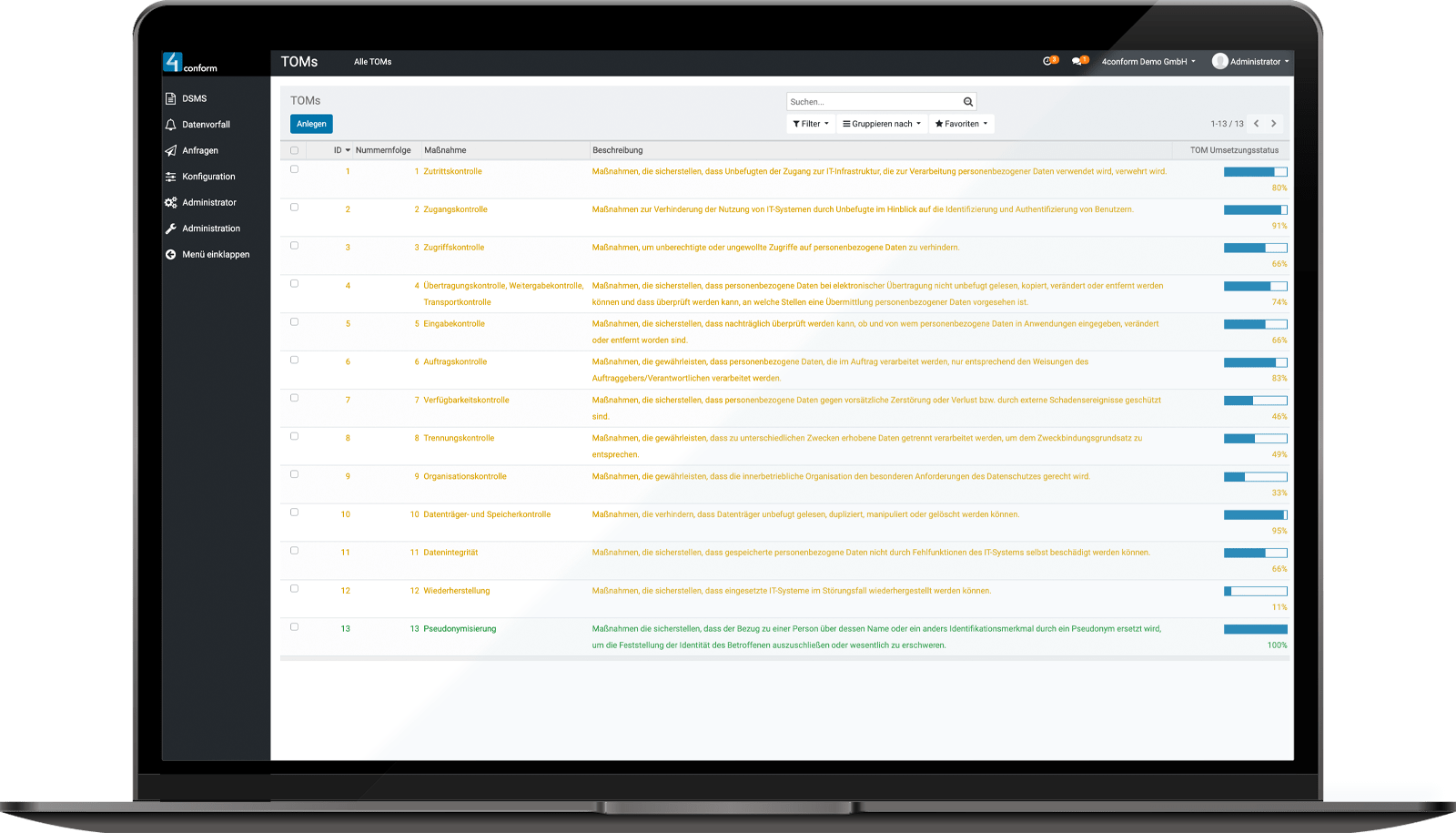
Map out your technical and organizational measures.
What our customers in the energy industry say
“Our standards for IT security and data protection are very high. With 4conform Enterprise, we have found a product that meets all the criteria. We were particularly impressed by the optimal implementation from the perspective of a processor, the comprehensive template package and the well thought-out role concept.”
Bundesrechenzentrum
Central IT service provider of the federal government

DSMS Live
Take a look at our DSMS in action
Book a demo now and find out how you can efficiently ensure the protection of sensitive data and meet legal requirements. In your demo appointment, we will show you how easy it is to integrate data protection into your company. Save your appointment and start into a more secure future!

What benefits does a DSMS offer?
Our ENTERPRISE DSMS software (data protection management system) is primarily used to ensure the protection and management of data in an organization. It focuses on compliance with data protection and data security regulations and the prevention of data breaches.
“Public administrations face the challenge of reconciling GDPR, NIS2 and BSI requirements – with limited resources. Our ENTERPRISE DSMS automates precisely these processes: from the documentation of processing activities to the reporting of data breaches within 72 hours. By integrating ISO 27001, authorities can finally manage information security and data protection in combination – with clear workflows for risk analysis, implementation of measures and reporting.”

Full security with 4conform
Information and data security is a complex topic. But it doesn’t have to be complicated. Learn more about our smart GRC and information security solutions and schedule a free initial consultation.












